由于犯罪分子利用各种方法来避开传统的刑侦图像技术, 因而红外图像逐渐成为获取犯罪现场痕迹的有效手段。 然而, 从犯罪现场拍摄的红外图像其目标痕迹大多是弱化的, 所以在这类红外图像中分割目标是一项具有挑战性的任务。 已有基于生物免疫的各类算法尚未明确描述免疫分割作用领域, 以及免疫网络算法模型中的免疫识别距离。 为实现对目标痕迹弱化红外图像的有效分割, 提出了一种新的具有免疫作用领域和最小平均免疫识别距离的人工免疫构架, 设计了一种具备最小平均距离免疫域的免疫分割算法。 该方法根据红外图像的特点, 采用多步分类算法、 免疫变异和自适应免疫最小均距识别方法, 根据目标区域和背景区域的总体统计特性实现最佳分类。 实验结果表明, 提出的基于最小平均距离的免疫算法能够有效地分割目标弱化的红外图像。 与经典的边缘模板和区域模板方法相比, 该算法具有更好的分割效果, 尤其是针对目标弱化红外图像的分割, 该算法能够较好地给出五个手指的边界轮廓。
Criminals tend to use various methods to cope with the traditional forensic image technologies, so infrared image is becoming an effective means for obtaining crime scene traces. However, segmentation targets from infrared image shoot in crime scene is a challenging task as these images are target weakened infrared images. Previous studies about immune algorithms do not describe immune variation and immune recognition distance in the network and algorithm. In opposition to segment these target weakened traces infrared images, we propose a new immune framework with immune variation and minimum mean immune recognition distance, and construct a new immune segmentation algorithm with minimum mean distance immune field. According to the distinguishing feature of infrared images, this method use multi-step classification algorithm, immune variation and adaptive immune minimum mean distance recognition to achieve optimal classification based on the overall statistical properties of target areas and background areas. Experimental results show that the proposed immune algorithm with minimum mean distance can segment target weakened infrared images efficiently. Compared with classical edge template and conventional region template methods, the proposed algorithm has better segmentation results, especially the boundaries of five fingers.
The existing evidence collection techniques for fingerprints and traces are usually invasive. Consequently, the original evidence in the crime scene tends to be damaged. As one of the most important materials for detecting and searching crime scene evidence, forensic image has become a research focus in recent years. With the development of technology, criminals have a better understanding of the general principle and mechanism of forensic images. Criminals are likeyl to use various methods to avoid traditional forensic image technologies, such as wrapping their hands with gloves and plastic bags to eliminate the hand traces. These methods, make it hard to obtain valid information via traditional forensic images, which means valid information can not be gained.
Faced with these challenges, infrared image is becoming an effective means for obtaining crime scene traces. Even criminals use various methods to rid the traces left at the crime scene, the infrared image is still able to get enough valid information. However, for these crime scene marks destroyed by criminals, the infrared images we are able to obtainare extremely blurred infrared images compared to ordinary infrared image. The target areas of these depth blurred images are seriously affected in two cases. The target area marks is weakened in the first case. Traces of the target area being weakened, and the difference between them and traces of the background areas is no longer obvious. Because the traces intensity of the background area maybe stronger than the target area which is extremely weakened, therefore, we call such images as target weakened traces infrared images. Target area is severely damaged in another case, such as wiping, or external influence. It is difficult for target area of such images to reflect the real target outline, therefore these images are called target drift traces infrared images. Therefore, segmentation of target weakened traces infrared images and target drift traces infrared images is a new theoretical and application problem for image processing and criminal Investigation.
There are many segmentation methods for different kinds of images[1, 2]. Akata Z proposes to view attribute-based image classification as a label-embedding problem: each class is embedded in the space of attribute vectors. Gharipour A proposes an integrated framework consisting of a new level sets based segmentation algorithm and a touching-cell splitting method to segment cell nuclei in fluorescence microscopy images[3]. Girshick R gives a simple and scalable detection algorithm that improves mean average precision (mAP) by more than 50 percent relative to the previous best result on VOC 2012-achieving a mAP of 62.4 percent[4]. Christodoulidis A proposes a new hybrid method for the segmentation of the smallest vessels, Line detection and perceptual organization techniques are combined in a multi-scale scheme[5]. Shi YH presents a novel semi-automatic learning-based prostate segmentation method, for segmenting the prostate in a certain treatment image, the radiation oncologist will be first asked to take a few seconds to manually specify the first and last slices of the prostate[6]. Zanetti M addresses the numerical minimization of a second-order functional for image segmentation, which exploits a compact matricial formulation of the objective functional and its decomposition into quadratic sparse convex sub-problems[7]. Kim S formulates a hypergraph-based image segmentation framework in a supervised manner for many high-level computer vision tasks, to consider short-and long-range dependency among various regions of an image and also to incorporate wider selection of features, a higher-order correlation clustering (HO-CC) is incorporated in the framework[8]. Akselrod-Ballin A presents a novel approach for whole body segmentation of small animals in a multimodal setting of MR, CT and optical imaging. The algorithm integrates multiple imaging sequences into a machine learning framework, which generates supervoxels by an efficient hierarchical agglomerative strategy and utilizes multiple SVM-kNN classifiers each constrained by a heatmap prior region to compose the segmentation[9].Kumar MP considers the problem of parameter estimation and energy minimization for a region-based semantic segmentation model, and addresss this problem by designing an accurate linear programming based approach for selecting the best set of regions from a large dictionary[10].
In past years, methods based on minimum distance have attracted more and more attention. Zhu ZC proposes a blind modulation classifier that differs from most existing classifiers, a low complexity minimum distance centroid estimator is suggested to estimate the channel gain and carrier phase jointly[11]. Bett SK Monitor urbans sprawl using minimum distance supervised classification algorithm in Rustenburg, South Africa, the algorithm is used to classify four land cover classes and post-classification method adopted for change detection[12]. Kapetanovic D numerically optimizes the multiple-input multiple-output (MIMO) precoders by making use of a state-of-the-art technique for optimization over the unitary group[13]. Ghimire S introduces a new method of image pixel classification based on minimum distance and hypothesis testing, the method is a nonparametric classification method which uses combined evidence from the multiple hypothesis testings and minimum distance to carry out the classification[14]. Nasibov E proposes two kinds of simple minimum distance-based classifier methods, these methods and known K-nearest neighbor (KNN) classification algorithm have been performed in order to classify enzymes according to their amino acid composition[15]. Srivastava MS presents a classification rule based on the minimum distance to classify an observation vector into two or several groups, and introduces a sample-squared distance between the two groups using Moore-Penrose inverse[16]. Silva WB assesses a new classifier for Polarimetric SAR (PolSAR) images, which input consists of segments, and each one is assigned the class which minimizes a stochastic distance[17]. Chen YC puts forwards distance-based margin support vector machine for classification, which gives the use of modified slack variables within the SVM (MS-SVM) to solve complex data problems, including class imbalance and overlapping[18]. Kahraman HT explains and extends a powerful similarity measurement method, which is called the fuzzy distance metric, to measure the distances between the test and training observations[19].
These algorithms have good segmentation results for different kinds of images, but they are not apply to the target weakened traces infrared images, the first case of the depth blurred infrared images, and cannot effectively solve a variety of criminals’ escape means. Thus, in opposition to the target weakened traces infrared images, we propose a new immune algorithm with minimum mean distance immune field for image segmentation. According to the distinguishing feature of target weakened traces infrared images, this method use multi-step classification algorithm to achieve optimal classification based on the overall statistical properties of target areas and background areas. Through the above steps, this algorithm realizes efficient image segmentation for target weakened trace infrared images.
In order to maintain the physical health, immune factors of biological immunity should identify its own cells and the outside world invading viruses or harmful bacteria, and kill the harmful bacteria and viruses. However, with long-term evolution, viruses and harmful bacteria can evade most of the innate immunity, thus harmful viruses and bacteria can invade the body. The long-term evolution viruses and harmful bacteria already have a great deal of resistance for immune effect molecule in innate immunity. To address the intrusion problem of long-term evolution viruses and bacteria invade, immune system gradually evolves adaptive immunity based on the innate immunity.
Although the long-term evolution viruses and harmful bacteria can evade extermination of innate immune effect molecule, they must exist certain features or some integrated features, which are consistent with the non-evolution bacteria and viruses. Thus, in close collaboration with the innate immunity, the adaptive immune can selection, extraction, and integration the same features between invasion harmful bacteria, viruses and its own cells. If the immune system trains and recognizes these features from a global statistical point of view, it will be able to guarantee the health.
In our previous study, we have given preliminary immune algorithms, but we have not describe immune variation and adaptive immune minimum mean distance recognition in the network and algorithm[20, 21, 22]. In the present paper, we construct a new immune segmentation algorithm with minimum mean distance immune field. Fig.1 shows the whole flow chart of our algorithm.
Innate immunity is the frontier of the immune system, it can rapidly identify and kill viruses and harmful bacteria which invading the body. in the long evolutionary process, the viruses and harmful bacteria invade the body and gradually differentiate into two categories. The first is a conservative evolution of viruses and harmful bacteria, this kind of harmful viruses and bacteria, while serious influence the health of the body , but their recognition characteristics did not change, and they can be quickly identified and killed by innate immunity. The second is the long-term evolution of viruses and harmful bacteria, such as the virus does not have a conservative molecule, bacteria with a protective cystic. In order to invade the body, and damage the health, this kind of viruses and harmful bacteria constantly change their recognition characteristics. It is difficult for innate immunity to identify the characteristics of these changes, so innate effect molecules can not kill these viruses and harmful bacteria. The underlying cause of this phenomenon is that the innate immune dependent on embryo genes encoded receptor to identify microorganisms, and these organisms tend to evolve more rapidly than the infected host itself.
However, these long--term evolution viruses and harmful bacteria , such as the virus does not have a conservative molecule, bacteria with a protective cystic , can still be processed and presented by innate immune factors through non--pattern recognition. Thereby the molecules of these viruses and bacteria that exhibit their infective properties are exposing. These immunological samples are identified by innate immunity, which can be pattern classified by innate immunity to the conserved evolution viruses and bacteria. Samples that can not be identified by innate immunity become long--term evolutionary viruses and bacteria. According to their own pattern recognition receptors, innate immunity classifies conserved evolutionarily viruses and bacteria.
Evolved viruses and bacteria have evolved their features identified by innate immunity, for example, harmful bacteria evolves and it has a protective encapsulation. At this point, innate immunity can not identify and kill these viruses and bacteria through the pattern recognition receptors. However, evolutionary viruses and bacteria must have certain characteristics or certain integration characteristics that are necessarily consistent with non-evolved viruses and bacteria. These characteristics become infectious characteristics, because with these infectious characteristics, evolution viruses and bacteria can cause damage to the health of the body.
Innate immunity can deal with these viruses and harmful bacteria, and these processes are not based on their pattern recognition receptors. The purpose of these treatments is to make the infection characteristics of these viruses and harmful bacteria manifest. For example, the removal of protective cysts of harmful bacteria. The characteristics of these viruses and bacteria are different from those pattern recognition characteristics recognize by the innate immune effector. Therefore, the characteristic extraction of these viruses and bacteria is affected by the effect molecules of innate immunity.
After the extraction of characteristics from these viruses and harmful bacteria, the impact of immune mutations should also be taken into account. Viruses do not have conserved molecules, and some of the harmful bacteria evolve very quickly, so these infection characteristics can change in a variety of ways. Although these changes will not affect their underlying infection characteristics, but it is a big problem for the recognition of the immune system. Therefore, we must take into account of the effects of immune mutations in the process of extracting characteristics from long-term evolutionary viruses and harmful bacteria.
The average characteristics of these viruses and harmful bacteria will undergo an ecological process of change, including open operation, closed operation, corrosion operations, expansion operations. This shows that long-term evolution of viruses and harmful bacteria, will evolve in different evolution directions to break through the defense of the immune system, affecting the body’ s health and balance.
f is used to represent a target weakened traces infrared image, f(u, v) represent the pixel gray value of pixel (u, v), u=1, 2, …, R is the row of the infrared image, v=1, 2, …, C is the column of the infrared image. b is the structural element for f, Db is the definitional domain of b. Specific immune features variation include the following:
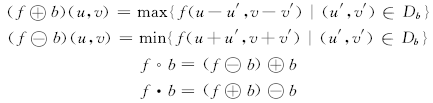
After identifying the characteristics of long-term evolution viruses and harmful bacteria, that is, their infection characteristics, it is necessary to adaptive identification and process these viruses and harmful bacteria. The adaptive immune recognition factor based on the results of innate immune recognition, non-long-term evolutionary viruses and harmful bacteria, to generate a pool of identified training antigens.
Because of the infection characteristics of non-long-term evolution viruses and bacteria did not change significantly, such as some harmful bacteria did not produce protective cysts, and can be recognized by innate immunity. Thus, features extracted from these non-long-term evolutionary viruses and bacteria are capable of reflecting the infection characteristics of viruses and bacteria. So it is not necessary to mutate the characteristics of this part of the virus and bacteria.
This nature of non-long-term evolutionary viruses and harmful bacteria, is called the invariance of infection characteristics. This invariance has two meanings, the first layer of indicating that if things fall in to the same class, its surface consistency characteristics can be used to extract characteristics for training and recognition. The second implication is that things belonging to the same class have not only the consistency of surface features, more importantly, they have the consistency of latent identity, which is the key point in deciding which of these things belong to the same category. In other intelligent algorithms, the use of surface features is very common. However, in the immune system, not only the antigen surface features are used, but also the potential characteristics of the antigen are fully presented. So in the identification of antigen and its own cells, the immune system can show excellent biological intelligence system characteristics, such as memory, tolerance, recognition and learning.
The minimum average immune domain algorithm is as follows:
Antigen production stage: According to the surface characteristics of the virus and the harmful bacteria, they can be recognized by the innate immune pattern recognition receptors. The initial image segmentation set is divided into antibody generation antigen set and antibody detection antigen set. The surface molecular patterns of the antibody-producing antigens are generally as follows:
f is the target weakened traces infrared image, the surface molecular patterns of the antibody-producing antigens are
where q=1, 2, 3, p=1, 2, 3, k is an integer, which determines the location of ϕ k-2q along the q. l is an integer, which determines the location of ϕ k-2q along the p. ϕ is a one-dimensional scale function, which is determined by Daubechies filter.
Adaptive antibody production stage: According to the surface molecule model of antibody-producing antigen, to generate adaptive antibodies, that is, adaptive immune factors. A portion of the adaptive immune factor is randomly generated, which has the same characteristic spatial dimension as the antibody-producing antigen. Each of the adaptive immune factors can divide the space of the antibody-producing antigen, that is, part of the antigenic space is partitioned. From this part of the adaptive immune factors, select the most effective one as the adaptive immune factor in this step, and the antigenic feature space determined by this factor is also fixed. The most efficient classification includes the most antigen, the most uniform antigen distribution, the best antigen aggregation and other criteria.
Repeating this process until all of the adaptive immune factors are selected and the feature space of the antibody-producing antigen is partitioned. All antigenic spaces have a category marker, and this class tag is unique. All antigens in the same partitioned feature space have the same class label, meaning that they belong to the same class of antigens. Other space parts adjacent to this part of the space have different categories of standard, that is, antigens in these spaces have different types of antigen.
Antigen aggregation stage: If all the antigens belonging to different parts are used as antigens for antibody production, then two problems will arise. First of all, some antigenic features space will contain a lot of antigens, making the calculation very complex and low efficiency in the process of generating antibodies. Secondly, if the number of antigens contained in a certain part of the antigenic space is too large, the distribution of the edge will be very irregular, and the production of adaptive immune factors will be more restrictive. Therefore, at this stage, the antigens in all of the feature space portions are aggregated. The rules for aggregation are as follows:
Suppose gi (i=1, 2, …, N) belongs to the k-th part of antigenic features space of antibody production antigens, then all the antigens were aggregated to an average point gk.
Adaptive antibody effectors generation stage: The effect factors of adaptive antibodies can be used to efficiently classify the aggregated antibody-producing antigens. First, partial effect factors are randomly generated to divide the mean points of the same class. The effect factor with the largest mean value is taken out as the predicted effect factor, and the average point divided by the effect factor is deleted. The next effect factors are generated randomly, and the effect factor with the largest mean value is taken out as the predicted effect factor, and the average point divided by the effect factor is deleted until only the last mean value point is left.
This division is not only able to achieve the antibody generation antigenic feature space division, but also to achieve the mean-based equidistant partition
When criminals wrap their hands with plastic bags, the infrared image will become target weakened traces infrared image, and the vast majority of criminal investigation means cannot obtain valid information. However, this method is increasingly being used by criminals.
Under laboratory conditions, we shot target weakened traces infrared image when a hand is wrapped with a plastic bag, as shown in Fig.2(a), and we shot hand trace infrared images when the hand leaves for 1 second, 30 seconds and 1 minute, as shown in Fig.2(b), Fig.2(c) and Fig.2(d), respectively. Fig.2(b) can reflect the touching contour between the hand wrapped by a plastic bag and the wall. But Fig.2(b) usually can not be obtained in crime scene because we can not get there in one second. The image we often get is Fig.2(d), which is a target weakened traces infrared image and its gray level can not reflect the valid information.
The proposed immune algorithm with minimum mean distance immune field has been simulated in MATLAB program environment for target extraction from target weakened traces infrared image.
Fig.3 shows the extraction results of different algorithms for banded blurred hand trace infrared image. (a) is the hand leaves the gun for 1 second and for 1 minute. (b) is the extraction result of Roberts. (c) is the extraction result of Prewitt. (d) is the extraction result of Sobel. (e) is the extraction result of Log. (f) is the extraction result of Canny. (g) is the extraction result of region growing algorithm. (h) is the extraction result of watershed algorithm. (i) is the extraction result of immune algorithm with minimum mean distance immune field.
From the segmentation results, we can seen that in these cases with target weakened traces, roberts, sobel, prewitt, Log, canny and region growing algorithm perform poorly, and can not extract hand area from the image. Watershed algorithm performs better but it still produces inaccurate hand boundary contours, and the outline of the five fingers, especially the little finger is very unclear, inaccurate. On the contrary, immune algorithm with minimum mean distance immune field proposed can produce more accurate hand target contours, especially the five fingers.
Overall, after analyzing the extraction performance of the algorithms mentioned above , immune algorithm with minimum mean distance immune field gives the best segmentation result for target weakened traces infrared images.
Segmentation of target weakened traces infrared images is a new theoretical and application problem for image processing and criminal investigation. In this paper, we propose a new immune algorithm with minimum mean distance immune field for target weakened infrared image segmentation. This method use multi-step classification algorithm to achieve optimal classification based on the overall statistical properties of target areas and background areas. Besides, the immune variation and adaptive immune minimum mean distance recognition is presented, which will make sure that the extraction method would be appropriate for the target weakened traces infrared images.
The visual results using our proposed immune algorithm with minimum mean distance are compared with those using other image segmentation methods including classical edge detection operator, region growing algorithm, and watershed algorithm. The comparison results show that the proposed method can get good extraction results, especially the boundaries of five fingers, on target weakened traces infrared images.
The authors have declared that no competing interests exist.
| [1] |
|
| [2] |
|
| [3] |
|
| [4] |
|
| [5] |
|
| [6] |
|
| [7] |
|
| [8] |
|
| [9] |
|
| [10] |
|
| [11] |
|
| [12] |
|
| [13] |
|
| [14] |
|
| [15] |
|
| [16] |
|
| [17] |
|
| [18] |
|
| [19] |
|
| [20] |
|
| [21] |
|
| [22] |
|





